Serverless Login
SRC: /mnt/ain lib -> https://library.m0unt41n.ch/challenges/serverless-login
Like the name indicates there isnt an actual backend, the sqlite3 db is delivered to the frontend combined with the python logic for auth.
The main concept is that the flag is encrypted and can only be decrypted with the valid password.
Based on the code we know, we somehow require the password... not the hashed value within the db (which we have access too)...
My crypto gapped dumbass started trying to somehow decrypting using the hash and googling weird crypto stuff, until it hit me.. it just a hash cracking typa thing...
Soo i read the hash from the db and then proceeded with john the ripper on kali with rockyou.txt too crack the hash.
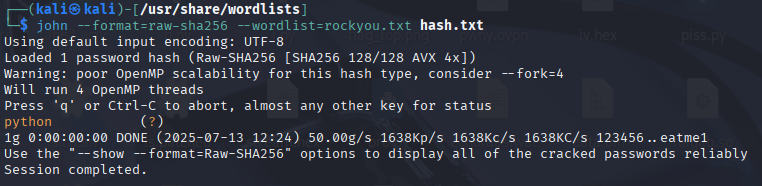
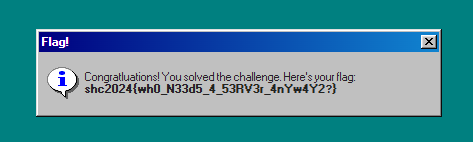
Boom boom boom, ye idk took me way too long...
SRC: /mnt/ain lib -> https://library.m0unt41n.ch/challenges/serverless-login
Like the name indicates there isnt an actual backend, the sqlite3 db is delivered to the frontend combined with the python logic for auth.
The main concept is that the flag is encrypted and can only be decrypted with the valid password.
Python:
def login(event):
db = sqlite3.connect("database.db")
username = document.querySelector("#username").value
password = document.querySelector("#password").value
passord_hash = hashlib.sha256(password.encode("utf-8")).hexdigest()
data = db.execute("SELECT * FROM login WHERE username=? and password=?", (username, passord_hash)).fetchone()
if data is not None:
master_key = int.from_bytes(bytes(password, "utf-8"))
cipher = aes.aes(master_key, 128, mode="CTR", padding="PKCS#7", iv=IV)
decrypted_flag = "".join([chr(x) for x in cipher.dec(FLAG)])
toggle("flag")
document.querySelector("#flag-text").innerHTML = f"Congratluations! You solved the challenge. Here's your flag: <b>{decrypted_flag}</b>"
else:
toggle("failed")Based on the code we know, we somehow require the password... not the hashed value within the db (which we have access too)...
My crypto gapped dumbass started trying to somehow decrypting using the hash and googling weird crypto stuff, until it hit me.. it just a hash cracking typa thing...
Python:
import sqlite3
IV = [189, 77, 180, 205, 234, 83, 27, 131, 247, 121, 193, 184, 101, 217, 98, 3]
FLAG = [165, 36, 84, 33, 185, 3, 234, 132, 91, 159, 25, 154, 54, 82, 30, 106, 205, 105, 209, 133, 77, 198, 132, 115, 70, 191, 129, 87, 48, 148, 186, 133, 30, 155, 115, 12, 19, 210, 220, 52, 68, 71, 81, 63, 43, 199, 53, 41]
db = sqlite3.connect("web/serverless-login/database.db")
data = db.execute("SELECT * FROM login").fetchall()
db.close()
print("[*] Loaded data from database:", data)
print("[*] User: " + data[0][0])
print("[*] Password Hashed: " + data[0][1])Soo i read the hash from the db and then proceeded with john the ripper on kali with rockyou.txt too crack the hash.
Boom boom boom, ye idk took me way too long...